1. Introduction
Wireless Sensor Networks (WSNs) [
1] consist of a large number of low-cost and energy-constrained devices. These devices transmit data acquired by a number of in-built sensors to one or several data collection units, named data sinks, which are in charge of sending data to remote database servers for further data processing and storage. Wireless Multimedia Sensor Networks (WMSNs) [
2] are regarded as a particular type of WSN where nodes are interfaced with sensors for visual and sound data acquisition, such as Complementary Metal Oxide Semiconductor (CMOS) cameras and microphones. This technology has drawn the attention of the WSN research community, encouraged by the challenge of providing support applications such as video surveillance, environmental monitoring, target tracking and traffic management, where multimedia services are required.
Compared with low-data-sampling, low-data-transmission rate WSN applications, multimedia applications impose stringent requirements in terms of high sampling rate, data transmission reliability, data latency and data throughput. Reliable transmission of multimedia data in WMSNs is challenging due to the inherent technology limitations, such as interference between devices or limited data transmission bandwidth. Multimedia communications also require a high utilization of the transmission channel, increasing communication activity within the network and considerably decreasing the operational lifetime of battery-powered nodes. This clearly contrasts with the traditional WSN/WMSN requirements imposed by, on the one hand, the use of short-range communications over low-bandwidth links (maximum bitrate of 250 kbps at 2.4 GHz) and, on the other hand, the energy constraints of sensor devices.
Traditional routing in WSNs is also a problem in WMSNs. Many state-of-the-art multi-hop proposals for WSNs consider tree-based topological configurations where only a few number of nodes are likely to forward all the data traffic. Because of the intensive use of these nodes, the network may not fulfil the Quality of Service (QoS) required by the multimedia application and, more importantly, it will lead to the overuse and depletion of the batteries of nodes in the path. In addition, traditional routing mechanisms usually only deal with the transmission to a sink node and not to any arbitrary node of the network, which hampers the development of collaborative applications or the use of multiple sinks.
Mesh topologies, in addition to enabling multiple routing paths between two nodes outside of radio communication range with each other, have proven advantages against other topological configurations, such as tree-based or cluster-based topologies, which include data transmission reliability, network robustness against node failures, and potential reduction in energy consumption [
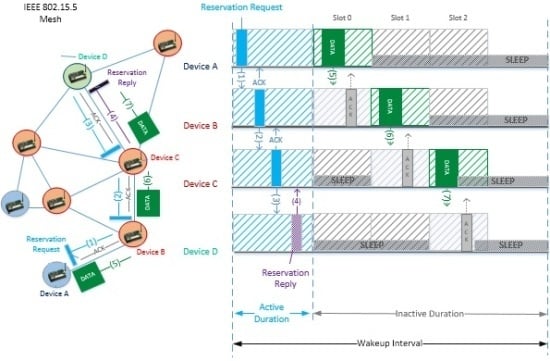
3]. Nodes arranged in a mesh topology are generally easier to deploy and potentially easier to maintain as they are able to reconfigure themselves in order to adapt to the conditions brought by the deployment environment. Among the different mesh solutions available for low-power wireless networks, the low-rate part of the IEEE 802.15.5 (hereafter IEEE 802.15.5) [
4] offers suitable functionalities for enabling multimedia applications compared with other state-of-the-art network/MAC layer standards. This standard assures that any node is able to communicate with any other node of the network through different routes, enhancing data transmission reliability and robustness against node failures. It also emphasizes simplicity, adding, for low-rate WPAN, a thin mesh sublayer on top of the IEEE 802.15.4 MAC sublayer, the most widely adopted point-to-point communication standard for low-rate wireless personal area networks (LR-WPANs). This results in an easy migration of applications using the 802.15.4 standard and in a greater scalability, enabling large-scale deployments. In addition, the standard provides two radio duty-cycle mechanisms, named Asynchronous Energy Saving (ASES) and Synchronous Energy Saving (SES). These mechanisms are intended to make efficient use of the available battery energy for, respectively, asynchronous and synchronous communications, thereby prolonging the battery life. For all the aforementioned reasons, IEEE 802.15.5 can be, a priori, a suitable and representative WMSN solution for the transmission of video in mesh topologies.
However, according to our knowledge, there are very few studies in the scientific literature combining mesh topologies with multimedia applications for low power devices. Under these circumstances, the purpose of this paper is to contribute to the development of multimedia applications in the WMSN arena, fulfilling the WSN/WMSN specific requirements, assuring the QoS of the multimedia service and achieving a reasonable performance of the network in terms of, for instance, lifetime and data transmission reliability. To achieve these goals, we have designed a novel tool, available for download, that evaluates, by means of computer simulation, the performance of video transmissions using the SES energy-saving mechanism of IEEE 802.15.5. For the evaluation of the standard, Quarter Common Intermediate Format (QCIF) video sequences are encoded using the H.264/AVC compression standard and transmitted through WMSN mesh networks of different sizes. The main results will be discussed, highlighting the most important metrics such as latency, jitter, time between packets, message delivery ratio, power consumption, lifetime and Peak Signal-to-Noise Ratio (PSNR). The rest of this paper is organized as follows:
Section 2 introduces related work in the field of WMSNs.
Section 3 provides the necessary technological background about video encoding with H.264 as well as WMSN operation based on the IEEE 802.15.5 standard.
Section 4 describes the simulation tool and simulation environment.
Section 5 shows and analyzes simulation results, which are further discussed in
Section 6.
Section 7 concludes this work.
2. Related Work
In spite of the proven advantages arising from the use of the IEEE 802.15.5 standard, to the knowledge of the authors, there is no other work that makes use of this technology in WMSNs. There are however a number of proposals that use mesh communication for transmitting multimedia flows [
5]. However, they do not consider Wireless Sensor Networks but rather focus on less energy-constrained standards such as 802.11. In this regard, the purpose of this work is twofold: first, to carry out a first evaluation of the performance of a mesh standard, the IEEE 802.15.5, for video transmission; second, to provide simulation tools to help evaluate further improvements for multimedia transmission made to the original standard.
The performance of WSNs and WMSNs should be assessed using real WSN/WMSN hardware before actual deployment, for example, using a test bed in the laboratory. However, it is best practice to make sure that no software/hardware errors are introduced before test-bed experiments are carried out. Finding and correcting these errors is usually a tedious and time-consuming task, and simulation is a powerful tool that helps do this in a much faster and easier way than dealing directly with hardware. In this regard, Pham [
6] studied the communication performance of the most popular WSN commercial platforms to date in data-intensive applications. Results showed significant delays limiting the maximum data throughput at both the sender and the receiver. The best results were obtained using MicaZ devices [
7]. Pham also showed that more effort should be made on the development of new hardware platforms, but also that more realistic simulation models are needed to consider the constraints of these commercial devices. Farooq
et al. [
8] studied the feasibility of performing the evaluation of new multimedia proposals in large WSN testbeds available for research usage. They concluded that, despite the existence of powerful hardware platforms for multimedia applications, there has been little work yet to integrate them into testbeds. Consequently, simulations are the most cost-effective solution for evaluating WMSN proposals.
Some researches focused on comparing the performance of data-intensive WMSN applications using different MAC and network protocols for diverse layouts. Ammar
et al. [
9] compared the performance obtained in WMSN by using two well-known WSN MAC protocols, S-MAC and 802.15.4, and two routing protocols, Ad hoc On-Demand Distance Vector (AODV) routing and its extension Ad hoc On-demand Multipath Distance Vector (AOMDV) routing. They remarked on the importance of optimizing the network layer protocols. In addition, their simulation results showed a better performance of the IEEE 802.15.4 standard in terms of network lifetime, which is supported by the large number of WMSN proposals based on this standard. Andrea
et al. [
10] studied this standard in one-hop data-intensive networks with star topology. They simulated a video surveillance system by continuously transmitting images to a sink node. Among other outcomes, their study determined that the Packet Error Rate for this kind of traffic, where packets have the maximum size allowed by the IEEE 802.15.4 standard, presents a significant increase as the network grows in comparison with typical WSNs with scalar sensors and short packets. In the same line, Pekhteryev
et al. [
11] performed a similar research in ZigBee networks that showed the difficulties in transmitting images over multi-hop networks. Although they only compared one-hop and two-hop schemes, they observed an important decrease in the percentage of recoverable images at the receiver for the two-hop scenario (from 2.6% to 20.5% using JPEG images, while for JPEG 2000 images the tests for the two-hop scenario could not completed due to interferences from other nodes).
There are other studies that focus on optimizing wireless performance communication in WMSNs in different ways. One of them considers cross-layer approaches to improve QoS. García-Sánchez
et al. [
12] used application-level QoS parameters to tune the MAC and physical layers of the popular IEEE 802.15.4 standard. An important increase in the maximum throughput for one-hop multimedia transmissions was achieved by means of a series of optimizations which maximized the amount of data transmitted and avoided collisions due to imperfect synchronization and other issues. In addition, the proposed solution remained compliant with the original standard. Farooq
et al. [
13] proposed another cross-layer architecture for multi-hop clustered networks where, upon congestion, nodes are requested to reduce the data transmission rate to avoid congestion. The authors used a differentiated services approach that classifies data traffic according to six different classes and where nodes producing less data and low priority data are penalized more than those producing high volumes of data and high priority data. Alanazi
et al. [
14] evaluated other QoS routing protocols for real-time WMSN applications, among which the Pheromone Termite (PT) protocol [
15] offered better performance. The protocol, though, relies on both ad-hoc MAC and, more importantly, physical layers, which makes its implementation on real devices very difficult.
In video transmission, the importance of each video frame can be used to select different QoS profiles. Kandris
et al. [
16] developed a video distortion model that made it possible to predict the effect on video quality of dropping each packet. In case of congestion, typically found when transmitting multimedia flows, this model is used to selectively drop less significant packets prior to transmission, therefore improving performance at the expense of additional computing load. The authors also used a hierarchical routing protocol with asymmetrical communications, where the sink is able to transmit directly to all nodes, with no intermediary hops. Zaidi
et al. [
17] developed a multipath protocol that obtained three different paths toward a sink node and, based on Bit Error Rate and delay, selected the best of them for the transmission of the most important video frames (the I frames, explained in
Section 3).
In general, multipath communication has traditionally been used to increase robustness or reliability in WMSNs. For example, the MMSPEED protocol [
18] uses probabilistic multipath forwarding to control the number of paths based on the required delivery probability. In this way, depending on the packet loss rate and QoS requirements, it can send multiple copies of a same packet to ensure the delivery of data. In WMSNs, multipath can also be used to increase the throughput in data-intensive flows. Teo
et al. [
19] proposed a routing protocol, I2MR, that transmits simultaneously through two paths. In order to avoid interference between them, the protocol uses the shortest path between source and destination as the primary path and marks one- and two-hop neighbors of nodes in the primary path as the interference zone. A secondary path as well as a backup path are then constructed using nodes outside the interference zone. This protocol is intended for less energy-constrained 802.11 networks, but there are similar proposals using more energy-constrained standards. Maimour [
20] developed the MR2 protocol. This protocol, which is better suited for dense WSN deployments, is also interference-aware, and constructs paths incrementally. After obtaining a new path, all of the nodes neighboring to the path, which potentially may cause interference, are notified and put in a passive mode and cannot be used for new paths. Therefore, avoiding interference and saving energy. Li
et al. [
21] proposed GEAM, a Geographic Energy-Aware Multipath routing scheme that divides the network into what the authors named “districts”. The distance between them is sufficiently large to avoid transmission interference. To send a packet, GEAM assigns the packet to a district and forwards it to the sink using the greedy algorithm. Consequently, it is necessary that each node is aware of its location. Bidai
et al. [
22] developed another multipath routing scheme for video transmission that combines proactive routing, which provides fast response to events of interest, with reactive routing. In this way, upon the detection of an event, the transmission of data packets to the sink starts immediately and, simultaneously, a route discovery phase begins where new paths to the sink are discovered. These paths are selected according to a metric defined by the authors that estimates their amount of interference. Simulation results demonstrate that selecting the less interfering path can increase throughput and decrease packet loss.
Table 1 shows the main contributions of the abovementioned proposals, as well as other features. As it can be observed, many of the proposals use either the IEEE 802.11 standard or the non-beacon mode of the IEEE 802.15.4 standard, which does not define how duty-cycling should be carried out. The 802.11 standard allows higher data transmission bit rates, therefore allowing for higher data throughput. However, it is not well suited for WSN because of its power consumption requirements. Similarly, 802.15.4 without a sleep/wake-up schedule,
i.e., duty-cycle, draws a considerably higher amount of power, albeit not as high as with 802.11. In the case of short-range transmissions, such as the typically used in WSNs, transmission power is lower than the power spent in reception mode [
23], therefore the most effective measure to limit power consumption is to make devices remain as much time as possible in low power (idle) states. For this same reason, battery-powered ZigBee-based solutions, where the non-beacon enabled mode is used, are known to have shorter network lifetimes simply because it forces all nodes with routing capability to be always on, with the subsequent battery drain. Finally, other routing schemes used in the discussed proposals exhibit other concerns. Hierarchical routing tend to overload nodes in the top layers of the hierarchy, which are closer to the sink, and, a priori, have more complex route repair procedures (
i.e., it takes some time to adapt to node failures, provided that the protocol is designed to perform route repair). Multipath schemes may overload some nodes if the path selection criteria lead to always choosing the same paths, potentially affecting network lifetime.
As stated before, the purpose of this work is to demonstrate the feasibility of video transmission using the IEEE 802.15.5 mesh standard, which is designed to create highly robust and reliable communication links. This standard allows for a very low power operation by defining how nodes should alternate periods of activity and inactivity to save energy and how these same nodes should coordinate with one another for a reliable transmission of data. This work is also intended to provide the scientific community with simulation tools for further evaluation of new protocols and improvements for WMSNs.
5. Performance Evaluation
The simulation results for every scenario (
Figure 7) are presented below. Different metrics of interest have been plotted, including latency, jitter, throughput, message delivery ratio, power consumption/network lifetime and PSNR. These metrics are commonly assessed in other studies related to multimedia traffic or WSNs. It should be noted that, for all scenarios, power consumption and lifetime were computed for node 1, as will be explained later in the text. To conclude this section, a scalability study is also included. It is intended to show the impact of the aforementioned metrics in networks composed of a large number of nodes and different node densities.
5.1. Latency
Latency has been computed as the average time between the generation of data messages and their delivery to the destination node (i.e., data sink). This includes the time dedicated by all the intermediate nodes belonging to the source–destination path for accomplishing tasks such as the data processing, temporary storage in the node's memory or transmission/reception procedures, among others.
The latency for all the packets that have successfully reached the destination is shown in
Figure 8. It can be observed that the latency shows a considerable variation for different values of WO. It should be noted that while the generation rate remains constant at 53 kbps, only one packet is transmitted per
wakeup interval, whose length is defined by this parameter. Consequently, as WO (and subsequently the
wakeup interval) increases, the capacity of the network to accommodate data traffic decreases and packets are stored in the queue of the first node waiting for transmission, therefore increasing the latency measured. Some simulations were also performed transmitting two packets per
wakeup interval, but the obtained performance was really poor. For example, for a 6 × 6 configuration, an increase in the latency of around 50% was measured. In this case, increasing the amount of data sent led to a higher contention for medium access, which worsened the performance of the network.
Under these circumstances, for any given WO–AO configuration, the latency increases linearly with respect to the number of transmitted packets (see
Figure 9) because of the packet service rate of the network (one packet per WI). The figure shows the evolution of the latency calculated after the arrival of each packet for a 6 × 6 network with a 5–3 (WO–AO) configuration. It has to be noted that latency values of zero in the figure represent packet loss.
In
Figure 8 there is a case that requires further explanation, specifically for AO = 1, where the latency measured is smaller. However, these low values are obtained because of high contention for medium access and the resulting packet loss. These figures must be analyzed in conjunction with the Message Delivery Ratio figures. For AO = 1, it can be observed that packet loss increases considerably since the
active duration is too short to successfully reserve all transmission slots. In particular, as the congestion of the network grows with time, most of the packets that are successfully received correspond to the first packets sent, which have a lower latency. On the contrary, packets sent subsequently, which have a higher latency as shown in
Figure 9, have a higher loss probability. Since the displayed latency is averaged over all the successfully received packets, this results in a deceptively short latency.
Besides, it can be observed that, for a fixed value of WO, the latency remains almost constant in the interval 3 ≤ AO < WO. Thus, a further increase of the
active duration will not have noticeable effects on the latency. This holds true even for AO = WO − 1, where the
inactive duration will still be long enough. According to
Table 5, for AO = WO − 1, the
inactive duration is as big as the active duration and thus adequate for transmission.
In conclusion, for a fixed value of WO, the latency remains almost constant except for the two following cases:
- -
For AO = 1 the active duration is too short and, given that the contention for the medium is too high, few nodes are able to reserve a slot for transmission and soon the network experiences congestion collapse. Packets are stored in queues (of infinite size) and many of them, due to the failure of the CSMA-CA mechanism (no successful transmission after the maximum number of retries), are discarded and will not reach the destination. The latency measured corresponds to the few packets that are successfully received.
- -
For AO = 2, the contention is still high (the inactive duration is not long enough yet) but packet loss is not as important as in the previous case (though still present). Therefore, the average delay represented is higher since the final packets (with higher latency) experience less congestion than for AO = 1. However, the latency measured is also slightly higher than for AO values greater than 2 because of the network congestion, as the transmission of packets may require more than one wakeup interval.
5.2. Inter-Packet Arrival Time
Inter-packet arrival time refers to the time that elapses from the receipt of a packet at the data sink to the instant at which the next packet is received.
According to the operation of the SES
reservation-based method, it can be expected that the time between the receipt of two consecutive packets at the destination node is determined by the time between slots that one particular node has available for transmission. This time is set by the length of the
wakeup interval, which, in turn, depends on the WO parameter. The theoretical inter-packet arrival time is:
Increasing the WO by one doubles the inter-packet arrival time, causing a decrease in throughput. This has been tested through simulations of a 6 × 6 network with WO–AO configurations in
Figure 10.
It can be observed that the obtained measurements are consistent with the theoretical values, with values around 0.16 s for WO = 5, 0.32 s for WO = 6 and 0.64 s for WO = 7. There are, however, small variations in the inter-packet arrival times, also known as jitter, which will be discussed in the next section. These variations are mainly due to the imperfect synchronization process performed in the SES mechanism and the CSMA-CA mechanism. In addition, larger variations, also caused by the CSMA-CA mechanism, may indicate packet delays through several wakeup intervals and, when packets arrive out of order, negative values may be found.
5.3. Jitter
Jitter is calculated as the variation in the inter-packet time caused by network congestion, packet loss, loss of synchronization, or by the use of multiple paths from source to destination. It must be noted that due to the use of the TDLS routing protocol, which by default selects the shortest paths between source and destination and performs load balancing across them, all the paths used for data forwarding will have the same number of hops. Therefore, in spite of the use of multiple paths, all the packets will traverse the same number of hops. Consequently, the jitter will not be affected.
However, there are situations where jitter is more likely to be affected. Analyzing
Figure 11, when
or
the jitter increases since the
active duration is insufficient to perform all slot reservations, resulting in more congestion and consequently in more unpredictable inter-packet arrival times.
5.4. Throughput and Message Delivery Ratio
Throughput is defined as the amount of raw information (header and payload) received in a given period. From this definition, it is clear that throughput is directly related to the message delivery ratio metric, that is, to the rate of successfully received messages. Consequently, these two metrics are discussed below jointly.
In order to evaluate the message delivery ratio, an entry is created in a text file for each message transmitted or received, as explained before, letting EvalVid check the number of packets sent and received.
It should be noted that UDP is used at the transport layer over the IEEE 802.15.5 mesh network layer and IEEE 802.15.4 MAC and PHY layers. Therefore, if a packet does not arrive at the destination node for whatever reason, the packet will not be retransmitted.
Since the size of queues has been assumed to be infinite, it can be deduced that packet losses are not related to the size of buffers. Consequently, packet losses are mainly caused by the occupation of the channel and the failure when accessing the medium through the CSMA-CA mechanism (no successful transmission after the maximum number of retries). In addition to existing medium contention, the exposed node problem and the hidden nodes problems also affect transmissions in the
active duration, since CSMA-CA does not avoid collisions by hidden nodes or unnecessary backoff delays by exposed nodes [
30]. The exposed node problem prevents a sender from transmitting to a receiver if the sender detects a signal from another node, even if that signal is not interfering at the receiver’s location. This increases the probability of CSMA failures. Besides, even if a node manages to transmit a message, it may be lost due to the hidden node problem. In this regard, the reservation process that takes place during the
active duration will be affected by both primary (two hidden nodes transmitting to the same receiver) and secondary (receiver in range of another node transmitting to a different node) collisions. On the other hand, the
inactive duration will be affected to a lesser extent by the hidden terminal problem, as discussed in
Section 5.6.
As observed in
Figure 12 and
Figure 13, AO values of 1 and, to a lesser degree, 2 present the worst performance in both the throughput and message delivery ratio. In addition, throughput is also affected by the selection of WO values, since it determines the separation between consecutive packets sent. That is, a longer
inactive period (or WO values) implies lower throughput. In particular, the best results for the throughput metric are obtained for 5–3 (WO–AO) configuration. In this case, the lengths of the
Wakeup Interval and Active Duration are found to be suitable for forwarding data messages without incurring long node delays.
5.5. Power Consumption and Lifetime
The SES mechanism provides an efficient energy-saving mechanism because the devices are sleeping most of the time, turning on their transceivers during short periods of time for transmitting or receiving video packets. In addition, according to the type of device in an IEEE 802.15.5 network (
i.e., whether the node acts as
mesh coordinator,
mesh or end device), it can be intuitively deduced which of them will have a higher power consumption during the
inactive period of the
SES reservation-based method:
Mesh coordinator: Most of its power consumption is due to the continuous performance of synchronization tasks [
28], which are out of the scope of this paper. Regarding data transmission power consumption, which is the focus of this section, the mesh coordinator will not have to perform data transmission and the only significant consumption is from packet reception during the allocated slots (it changes the radio transceiver state from
sleep to
listening).
End device: This type of device corresponds to the source node that sends packets continuously through the network. Therefore, its power is consumed during the transmission in one slot per SES time structure, that is, one slot for each wakeup interval.
Mesh device (router): Unlike the other two types of nodes, mesh devices require two consecutive slots of the inactive period, one for receiving from the previous node and another for transmission to the next node. Consequently, they are the devices that have the highest power consumption.
On the other hand, all nodes have additional power consumption during the whole active duration since their transceivers are either in the listening state or in the transmit state. Consequently, the active duration affects to a greater extent the power consumption metric than the inactive duration, where nodes remain asleep for most of the time (their state is switched only to perform the scheduled transmissions/receptions in the reserved slots).
It can be observed in all the evaluated scenarios—
Figure 14 and
Figure 15—how the AO has a considerable impact on power consumption (regardless of the WO, nodes configured with a low AO value consume less energy). It should be noted that both power consumption and lifetime metrics were calculated for node 1, which has a high power consumption as it is a mesh device and it is located close to the destination node where all the paths generated by the TDLS algorithm converge.
5.6. Peak Signal-to-Noise Ratio
The most widespread method to determine the quality of a video sequence is the Peak Signal-to-Noise Ratio (PSNR), which represents the ratio between the maximum possible power of a signal and the power of the distorting noise that affects the fidelity of its representation. Because many signals have a wide dynamic range, PSNR values are usually expressed in logarithmic scale.
In order to compute the PSNR, the
Mean Squared Error (MSE) of each frame must first be obtained. The MSE represents the cumulative squared error between the compressed frame and the original frame. For a monochrome image, it is calculated as:
where
corresponds to the value of the
pixel of the transmitted frame and
is the value of the same pixel in the received frame.
The PSNR is defined as:
where
MAX denotes the maximum possible pixel value of the image. If B bits are used per pixel (luminance component),
MAX = 2
B − 1.
Considering a video sequence composed of a series of frames, the MSE and PSNR are calculated for each of the frames and the PSNR of the complete video sequence is the mean value of the PNSR of the frames.
EvalVid uses the PSNR as an evaluation metric of the quality of compressed videos. When the difference between the frames of an original video sequence and the frames of the received and decoded video sequence is high, the PSNR is low. Therefore, higher values of PSNR denote better quality of the video. Acceptable values for wireless communication systems are considered to be about 20 dB to 25 dB.
On the other hand, for the subjective evaluation of video quality, the MOS (
Mean Opinion Score) [
36] is usually employed. This technique is based on the perceived quality from the users’ perspective of the received video (or any other kind of signal), giving a score to video sequences from 1 (worst) to 5 (best). In [
37] a possible mapping between PNSR and MOS values is provided. The conversion between the two metrics can be seen in
Table 7.
Above, in
Figure 16, the results of the PSNR for each of the simulated scenarios are shown. In view of the presented results, a degradation in the quality of the video can be observed as the network grows. Besides, the values of WO seem to have some impact for larger networks, 5 × 5 and 6 × 6, but not for small networks. In particular, the PSNR value deteriorates for lower WO values due to the hidden terminal problem. With fixed AO values and therefore fixed
active duration and contention for medium access, the only reason for this drop in performance is packet loss in the
inactive duration. Since there is no contention for medium access during this period, packet loss is due to the hidden terminal problem. More particularly, only secondary collisions from hidden nodes’ transmissions can take place, whereas primary collisions cannot happen because of the slot reservation process performed in the
active duration.
As a consequence of the above-mentioned, the size of the network has to be taken into account for the appropriate selection of the WO, finding a balance between the quality of the video and throughput (high WO values reduce the throughput considerably).
With respect to the AO parameter, the worst PSNR values are obtained for AO = 1 and AO = 2, since the large amount of packet losses distorts the quality of the decoded video. For 3 ≤ AO < WO there is little variation in the PSNR, implying a good or excellent video reproduction.
Comparing the three different video sequences, it can be easily deduced that, regardless of the network size, the PSNR gets worse for sequences with higher motion. However, this can be misleading, since the drop in quality is not as high as it may seem. This is due to the use of the CRF encoding method. CRF compresses different frames by different amounts, taking the motion into account. Therefore, frames with higher motion will have a greater compression, discarding more information from them. The reason for doing so is that the human eye perceives more detail in still objects than in moving objects. Consequently, in spite of having a worse PSNR because of greater compression, subjectively, the quality of the video sequences with high motion will still be acceptable. To this extent, the video sequences with higher motion, Foreman and Mobile QCIF, obtained after the simulation using a 5–3 (WO–AO) configuration for the 6 × 6 scenario can be seen [
38], where, although its quality is rated as “very annoying” according to the PSNR to MOS conversion, the video can be considered as acceptable from a subjective point of view.
5.7. Scalability
The evolution of the obtained performance metrics according to the size of the networks is shown in
Figure 17, ranging from 2 hops for a 2 × 2 network to 10 hops for a 6 × 6 network. All metrics remain within acceptable values for any network size, proving the scalability of the IEEE 802.15.5 SES mechanism for video transmission. For the largest network sizes, though, there is a small drop in performance. In these cases, increasing the value of the WI parameter will improve the quality of the received video at the expense of throughput.
6. Discussion
The previous section has shown the performance of IEEE 802.15.5 mesh networks transmitting with a packet generation rate of 53 kbps and dispatching one packet per wakeup interval, since transmitting more than one packet per wakeup interval was observed to lead to congestion and therefore worsen the performance of the network. In particular, the effect of using different WO–AO configurations for several network sizes has been studied.
In spite of considering that just a single node is transmitting video, the previous metrics show that there is some drop of performance because different packets of the same stream may be routed by different paths and compete for transmission. In this regard, the performance drop observed is due to repetitive failures to gain access to the medium while it is busy (CSMA-CA failure), aggravated by the exposed and hidden nodes problems. To cope with these problems, the reservation-based method of the SES mode proposes the use of a relatively short active duration period, where all contention for reserving transmission slots takes place, and the inactive duration, where nodes have slots where transmission is guaranteed. In data-intensive applications, though, this inactive period can also be affected by the hidden node problem to some degree, as mentioned.
During the active period, nodes have the opportunity to reserve slots for subsequent transmissions in the inactive period. Since the active duration of all neighbor nodes is synchronized, it is likely that several nodes will try to perform simultaneous reservations. In order to avoid collisions, the CSMA-CA scheme allows that, if some reservation message cannot be sent because the channel is busy, several subsequent retransmission attempts (up to a configurable maximum number in the IEEE 802.15.4 standard, macMaxCSMABackoff, 4 by default) can be performed. However, according to the simulations, AO values of 1 and 2 result in active durations not long enough to perform all CSMA-CA retries. For example, the maximum delay (in a worst case scenario) due to the CSMA-CA backoff is 36.8 ms (calculated as where ) using the IEEE 802.15.4 default values at 2.4 GHz, whereas for AO = 1 the active duration is only 10 ms long. This implies that several active durations may be necessary in order to reserve one transmission slot. However, during that time, new packets would also require to be transmitted, increasing the contention for medium access (if the packets are received by neighbor nodes) or the queue size of the node, and therefore the performance of the network would get worse as time goes on.
Given all the factors that affect negatively the transmissions during the active duration, it is clear that it is very important to select an AO value that allows transmission with an appropriate QoS. It has been observed for all the previous QoS metrics that for AO values equal to or greater than 3, the performance has been quite satisfactory. Taking into account that the AO parameter is detrimental to power consumption and network lifetime, a value of 3 can be used for the scenarios studied without affecting latency, jitter, throughput and message delivery ratio.
Regarding the selection of the
wakeup interval length, and consequently the WO parameter, it is important to find a balance between power consumption (which improves with high WO values) and throughput (which improves with low WO values). In addition, it has also been observed that the size of the network may affect the quality of the received video due to the hidden terminal problem, and more particularly secondary collisions. Other negative factors such as contention for medium access, the exposed node problem or primary collisions due to the hidden node problem are avoided by the use of transmission in reserved slots of the inactive period. Thanks to this fact, the drop of performance in the
inactive duration is not important and it is only noticeable for networks of size 5 × 5 and greater. As the size of the networks grows, the number of packet retransmissions in the mesh network increases, and therefore the probability of secondary collisions. For the scenarios studied, a WO value of 5 has shown to provide good video quality without worsening the throughput. This can be better observed by watching the received videos since, as mentioned in the previous section, values of PSNR values may be misleading for videos with high motion. It has to be noted that, due to the tendency of worsening PSNR and packet loss with network size, for networks larger than the studied ones, higher values of WO should be considered. In this case, increasing the WO by one implies a more than twofold increase of the
inactive duration and the number of slots (see
Table 5). Therefore transmissions in the
inactive duration are sparser and the probability of collision decreases.
In view of the simulation results, it can be affirmed that it is feasible to transmit video using the IEEE 802.15.5 standard. Using appropriate WO–AO values, it can achieve the necessary reliability for a satisfactory video quality. On the other hand, the main drawback of the standard is that it does not achieve high throughput values, which hinders its applicability to real-time video applications, although this is anyway very challenging for multi-hop networks. In order to improve throughput, some enhancements are necessary that allow more than one packet per wakeup interval to be reliably sent. This can be achieved by tackling the diverse problems that have been discussed in this section in order to arrange transmissions so that multimedia flows can use more than one slot per wakeup interval, but also by applying enhancements in the directions given in the Related Work section. In this line, the standard has an important feature, the possibility of allowing transmissions to any other node of the network, which facilitates the development of collaborative or multi-sink applications.
7. Conclusions
In this paper, the transmission of video sequences using the low rate part of the IEEE 802.15.5 standard has been evaluated by means of a new simulation tool which is available in [
33]. This tool implements the SES reservation-based method as energy-saving mechanism, following faithfully the standard specification. Furthermore, the simulation framework integrates the SES method and the EvalVid software, which generates compressed QCIF video sequences with different motion, encoded using H.264/AVC. These sequences are transmitted through mesh networks of different sizes. The main results of the simulations have been presented and discussed, highlighting the most important metrics such as latency, jitter, time between packets, message delivery ratio, power consumption, lifetime and PSNR. The importance of the selection of appropriate values for the
active order and
wakeup order parameters has been emphasized, observing that for
video transmission is feasible. A 5–3 (WO–AO) configuration has been found to be the best for the scenarios studied, although, for larger networks, higher WO values can be considered. The video sequence obtained after the simulation of 5–3 and 7–2 (WO–AO) configurations for Akiyo, Foreman and Mobile QCIF can be found at [
38,
39,
40,
41,
42,
43].
In addition, the developed tool can be used to evaluate different enhancements over the IEEE 802.15.5 standard. In spite of the advantages of this standard reported in this work, such as fault tolerance or the possibility that any node transmits to any other node, there is still room for improvement for data-intensive applications and, more particularly, WMSN applications. In this regard, it is possible to introduce enhancements to the original standard, with no detriment to the interoperability with other IEEE 802.15.5 devices, which take into account the particularities of WMSN and increase its performance for this type of application.