A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems
Abstract
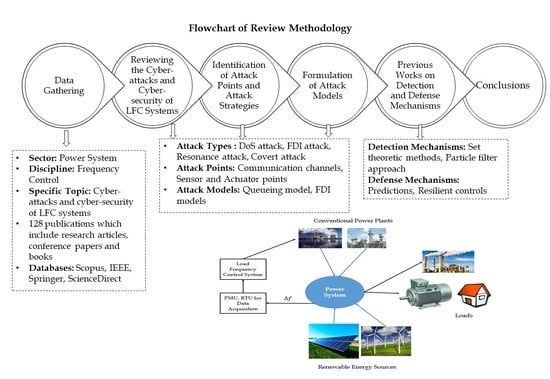
:1. Introduction
2. LFC System Configurations
2.1. Single-Area LFC Scheme
2.2. Multi-Area LFC Scheme
Two-Area LFC Scheme
- An increase in the load demand () in area j can result in the reduction of generator frequencies ( and ) and an increase in the power flow to area j.
- If the load demand () has increased in area i, then it would result in the reduction of generator frequencies ( and ) and power flow to area j.
- A reduction of load demand () in area j would result in the increase of generator frequencies and reduction in power flow to area j.
- A reduction of load demand () in the area i would result in the increase of generator frequencies and power flow to area j.
2.3. LFC Scheme with RES
3. Types of Attacks in LFC System
3.1. Sensor and Actuator Attack Model of LFC System
3.2. DoS Attack
3.2.1. Attacking Strategies of DoS and DDoS Attacks in LFC System
3.2.2. DoS Attack Model
3.3. Data Integrity Attack/Deception Attack
3.3.1. False Data Injection (FDI) Attack
- Ramp attack: Ramp attack involves the modification of output measurements or control signals using a gradually increasing or decreasing ramp function for an attack period . During the attack period, or will be equal to , where is the ramp parameter and .
- Pulse attack: Pulse attack involves the modification of output measurements or control signals using temporally spaced short pulses with some attack parameter . Further, can describe the pulse shape characteristics.
- Random attack: Random attack involves the modification of output measurements or control signals, over the attack time period, through the addition of values returned from a uniform random function . In this case, and , where represents the lower and upper bounds of or [75].
- Scaling attack: Scaling attack involves the modification of output measurements or control signals to higher or lower values based on the scaling parameter . In this case, the attack at the sensor and actuator channels can be represented as and , respectively. When the parameter is adjusted in such a way that or , then such kind of attack is called min attack, where and represents the minimum values of the output and control signals, respectively. When the parameter is adjusted in such a way that or , then it is called max attack, where and represent the maximum values of the output and control signals, respectively.
- Attacking physical sensors by sensor spoofing;
- Utilizing communication channels of sensor and actuator data;
- Compromising the computational algorithms of the control center;
- Compromising the logically isolated VPN channels from the distributed sensors;
- Global positioning system (GPS) spoofing: GPS spoofing allows penetration to PMU and affects clock synchronization of substations leading to wrong phase angle measurements.
- Through the collection of offline and online data using manual techniques or by deploying meters for accessing the grid;
- Using the market data related to the economic dispatch problem;
- Utilizing power flow measurements: The correlation among the power flow measurements provides topology information, when the system parameters like active and passive loads are varied.
3.3.2. Replay Attack
- Monitoring Phase : During the monitoring phase, the gathered sensor measurements are stored in ,
- Replay Phase : During replay phase, the collected sensor data is sent to the controller until the end of the attack,
3.3.3. Covert Attack
3.4. Zero Dynamics Attack
3.5. Resonance Attack
- Internal state of the plant: If the attacker is aware of the internal states of the plant (like governor output, turbine output, etc.), then a powerful attack can be launched through load modification according to the estimated state.
- Frequency Derivation: Frequency derivation is another resonance reference that allows the attacker to produce fake input for resonance attack. For instance, the attack input can be taken as as in [11], where is the frequency derivation.
3.6. Time-Delay Switch (TDS) Attack
4. Attack Detection and Defense Mechanisms
4.1. DoS Attack
4.2. FDI Attack
4.3. Replay Attack
4.4. Covert Attack
4.5. Resonance Attack
4.6. Time-Delay Switch Attack
5. Future Research
- Impact analysis of coordinated or hybrid attacks and the development of mitigation techniques for these attacks. Resource constraints, like bandwidth of communication channels, energy limitations, etc., should be also considered simultaneously during the development of attack detection and defense mechanisms, and then the security and service quality can be assured at the same time [21].
- Analysis of individual or coordinated attacks in LFC systems under noisy communication networks [20].
- Adequate attention and profound discussion is needed in the area of multiple attack strategies for the development of adaptive defense strategies against different types of attacks [21].
- The vulnerability to distributed attack strategies like DDoS is higher for geographically distributed control systems like LFC. Therefore, more effective coordinated defense strategies for cyber and physical layer has to be developed. ACL-based firework defense strategies of cyber layer applied in [70] have poor real-time performance.
- Extension of estimation and detection schemes to the stochastic model of the LFC system [120].
- RESs are gathering higher attention in the field of power systems due to their intermittent nature. Research in the field of cyber-security of LFC systems with integrated RES has to be performed further, as the impact of cyber-attacks can be worse in such kind of systems.
- Apart from analyzing various FDI attacks using the predefined attack templates, multi-step attack strategies adopted by attackers can be also considered for the impact analysis.
- Many of the resilient control techniques developed for defending data integrity techniques do not consider time-delays of the communication channel. The stability of the LFC system may not be affected by small time-delays [27]. However, it can affect the controller efficiency and attack estimation accuracy. Therefore, the defense techniques considering transmission time-delays have to be included in future research.
- Research works that analyze the effects of covert attacks in networked control systems like LFC are also highly encouraged as it seems to be an unexplored area. As the covert adversaries implement powerful and stealthy attack strategies it is high time to investigate the impact of such attack in LFC system and look for the development of countermeasures.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Ali, R.; Mohamed, T.H.; Qudaih, Y.S.; Mitani, Y. A new load frequency control approach in an isolated small power systems using coefficient diagram method. Int. J. Electr. Power Energy Syst. 2014, 56, 110–116. [Google Scholar] [CrossRef]
- Arbab Zavar, B.; Palacios-Garcia, E.J.; Vasquez, J.C.; Guerrero, J.M. Smart inverters for microgrid applications: A review. Energies 2019, 12, 840. [Google Scholar] [CrossRef] [Green Version]
- Shen, J.; Jiang, C.; Li, B. Controllable load management approaches in smart grids. Energies 2015, 8, 11187–11202. [Google Scholar] [CrossRef] [Green Version]
- Xiang, Y.; Lu, X.; Yu, Z.; Shi, D.; Li, H.; Wang, Z. IoT and edge computing based direct load control for fast adaptive frequency regulation. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5. [Google Scholar]
- Wang, Q.; Wang, H.; Zhu, L.; Wu, X.; Tang, Y. A Multi-Communication-Based Demand Response Implementation Structure and Control Strategy. Appl. Sci. 2019, 9, 3218. [Google Scholar] [CrossRef] [Green Version]
- Mateev, V.; Marinova, I. Distributed Internet of Things System for Wireless Monitoring of Electrical Grids. In Proceedings of the 2018 20th International Symposium on Electrical Apparatus and Technologies (SIELA), Bourgas, Bulgaria, 3–6 June 2018; pp. 1–3. [Google Scholar]
- Keyhani, A.; Chatterjee, A. Automatic generation control structure for smart power grids. IEEE Trans. Smart Grid 2012, 3, 1310–1316. [Google Scholar] [CrossRef]
- Saadat, H. Power System Analysis; McGraw-Hill: New York, NY, USA, 1999. [Google Scholar]
- Oshnoei, A.; Khezri, R.; Muyeen, S.M.; Blaabjerg, F. On the contribution of wind farms in automatic generation control: review and new control approach. Appl. Sci. 2018, 8, 1848. [Google Scholar] [CrossRef] [Green Version]
- Sridhar, S.; Hahn, A.; Govindarasu, M. Cyber–physical system security for the electric power grid. Proc. IEEE 2011, 100, 210–224. [Google Scholar] [CrossRef]
- Wu, Y.; Wei, Z.; Weng, J.; Li, X.; Deng, R.H. Resonance attacks on load frequency control of smart grids. IEEE Trans. Smart Grid 2017, 9, 4490–4502. [Google Scholar] [CrossRef]
- UCTE. Appendix 1: Load-Frequency Control and Performance. Available online: https://eepublicdownloads.blob.core.windows.net/public-cdn-container/clean-documents/pre2015/publications/ce/oh/appendix1_v19.pdf (accessed on 4 June 2020).
- Kirby, B.; Ela, E.; Milligan, M. Analyzing the impact of variable energy resources on power system reserves. In Renewable Energy Integration; Elsevier: Amsterdam, The Netherlands, 2017; pp. 85–101. [Google Scholar]
- Shen, Y.; Fei, M.; Du, D. Cyber security study for power systems under denial of service attacks. Trans. Inst. Meas. Control 2019, 41, 1600–1614. [Google Scholar] [CrossRef]
- Chatterjee, K.; Padmini, V.; Khaparde, S.A. Review of cyber attacks on power system operations. In Proceedings of the 2017 IEEE Region 10 Symposium (TENSYMP), Cochin, India, 14–16 July 2017; pp. 1–6. [Google Scholar]
- Sánchez, H.S.; Rotondo, D.; Escobet, T.; Puig, V.; Quevedo, J. Bibliographical review on cyber attacks from a control oriented perspective. Annu. Rev. Control 2019, 48, 103–128. [Google Scholar] [CrossRef] [Green Version]
- Pandey, S.K.; Mohanty, S.R.; Kishor, N. A literature survey on load–frequency control for conventional and distribution generation power systems. Renew. Sust. Energy Rev. 2013, 25, 318–334. [Google Scholar] [CrossRef]
- Dagoumas, A. Assessing the impact of cybersecurity attacks on power systems. Energies 2019, 12, 725. [Google Scholar] [CrossRef] [Green Version]
- Alhelou, H.H.; Hamedani-Golshan, M.E.; Zamani, R.; Heydarian-Forushani, E.; Siano, P. Challenges and opportunities of load frequency control in conventional, modern and future smart power systems: A comprehensive review. Energies 2018, 11, 2497. [Google Scholar] [CrossRef] [Green Version]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef] [Green Version]
- Mahmoud, M.S.; Hamdan, M.M.; Baroudi, U.A. Modeling and control of Cyber-Physical Systems subject to cyber attacks: A survey of recent advances and challenges. Neurocomputing 2019, 338, 101–115. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Mitigating the impacts of covert cyber attacks in smart grids via reconstruction of measurement data utilizing deep denoising autoencoders. Energies 2019, 12, 3091. [Google Scholar] [CrossRef] [Green Version]
- Vrakopoulou, M.; Esfahani, P.M.; Margellos, K.; Lygeros, J.; Andersson, G. Cyber-attacks in the automatic generation control. In Cyber Physical Systems Approach to Smart Electric Power Grid; Springer: Berlin/Heidelberg, Germany, 2015; pp. 303–328. [Google Scholar]
- Li, Y.; Zhang, P.; Ma, L. Denial of service attack and defense method on load frequency control system. J. Frankl. Inst. 2019, 356, 8625–8645. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.S.; Dong, X.; Yau, D.K.Y.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Optimal false data injection attack against automatic generation control in power grids. In Proceedings of the 2016 ACM/IEEE 7th International Conference on Cyber-Physical Systems (ICCPS), Vienna, Austria, 11–14 April 2016; pp. 1–10. [Google Scholar]
- Abbaspour, A.; Sargolzaei, A.; Yen, K. Detection of false data injection attack on load frequency control in distributed power systems. In Proceedings of the 2017 North American Power Symposium (NAPS), Morgantown, WV, USA, 17–19 September 2017; pp. 1–6. [Google Scholar]
- Abbaspour, A.; Sargolzaei, A.; Forouzannezhad, P.; Yen, K.K.; Sarwat, A.I. Resilient Control Design for Load Frequency Control System under False Data Injection Attacks. IEEE Trans. Ind. Electron. 2019, 67, 7951–7962. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z. False data attack models, impact analyses and defense strategies in the electricity grid. Electr. J. 2017, 30, 35–42. [Google Scholar] [CrossRef]
- Khalaf, M.; Youssef, A.; El-Saadany, E. Joint detection and mitigation of false data injection attacks in AGC systems. IEEE Trans. Smart Grid 2018, 10, 4985–4995. [Google Scholar] [CrossRef]
- Cheng, Z.; Yue, D.; Hu, S.; Huang, C.; Dou, C.; Chen, L. Resilient load frequency control design: DoS attacks against additional control loop. Int. J. Electr. Power Energy Syst. 2020, 115, 105496. [Google Scholar] [CrossRef]
- Bevrani, H. Robust Power System Frequency Control; Springer: Berlin/Heidelberg, Germany, 2009; Volume 85. [Google Scholar]
- Murty, P.S.R. Load Frequency Control. In Electrical Power Systems; Elsevier: Amsterdam, The Netherlands, 2017; pp. 651–700. [Google Scholar]
- Roy, S.D.; Debbarma, S. Detection and Mitigation of Cyber-Attacks on AGC Systems of Low Inertia Power Grid. IEEE Syst. J. 2019, 14, 2023–2031. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.S.; Yau, D.K.Y.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Modeling and mitigating impact of false data injection attacks on automatic generation control. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1609–1624. [Google Scholar] [CrossRef]
- Zhao, F.; Yuan, J.; Wang, N.; Zhang, Z.; Wen, H. Secure Load Frequency Control of Smart Grids under Deception Attack: A Piecewise Delay Approach. Energies 2019, 12, 2266. [Google Scholar] [CrossRef] [Green Version]
- Kontouras, E.; Anthony, T.; Dritsas, L. Set-theoretic detection of data corruption attacks on cyber physical power systems. J. Mod. Power Syst. Clean Energy 2018, 6, 872–886. [Google Scholar] [CrossRef] [Green Version]
- Franzè, G.; Tedesco, F.; Casavola, A.; Garone, E. A leader-follower architecture for Load Frequency Control purposes against cyber attacks in power grids-Part I and II. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016; pp. 5128–5139. [Google Scholar]
- Chen, C.; Cui, M.; Wang, X.; Zhang, K.; Yin, S. An investigation of coordinated attack on load frequency control. IEEE Access 2018, 6, 30414–30423. [Google Scholar] [CrossRef]
- Sridhar, S.; Manimaran, G. Data integrity attacks and their impacts on SCADA control system. In Proceedings of the IEEE PES General Meeting, Providence, RI, USA, 25–29 July 2010; pp. 1–6. [Google Scholar]
- Cheng, Z.; Yue, D.; Hu, S.; Xie, X.; Huang, C. Detection-based weighted H∞ LFC for multi-area power systems under DoS attacks. IET Control. Theory Appl. 2019, 13, 1909–1919. [Google Scholar] [CrossRef]
- Alrifai, M.T.; Hassan, M.F.; Zribi, M. Decentralized load frequency controller for a multi-area interconnected power system. Int. J. Electr. Power Energy Syst. 2011, 33, 198–209. [Google Scholar] [CrossRef]
- Daneshfar, F.; Bevrani, H. Multiobjective design of load frequency control using genetic algorithms. Int. J. Electr. Power Energy Syst. 2012, 42, 257–263. [Google Scholar] [CrossRef]
- Dong, L.; Zhang, Y.; Gao, Z. A robust decentralized load frequency controller for interconnected power systems. ISA Trans. 2012, 51, 410–419. [Google Scholar] [CrossRef] [Green Version]
- Bevrani, H.; Daneshfar, F.; Daneshmand, P.R. Intelligent automatic generation control: Multi-agent Bayesian networks approach. In Proceedings of the 2010 IEEE International Symposium on Intelligent Control, Yokohama, Japan, 8–10 September 2010; pp. 773–778. [Google Scholar]
- Adaryani, M.R.; Afrakhte, H. NARMA-L2 controller for three-area load frequency control. In Proceedings of the 2011 19th Iranian Conference on Electrical Engineering, Tehran, Iran, 17–19 May 2011; pp. 1–6. [Google Scholar]
- Vrdoljak, K.; Perić, N.; Petrović, I. Sliding mode based load-frequency control in power systems. Electr. Power Syst. Res. 2010, 80, 514–527. [Google Scholar] [CrossRef]
- Prakash, S.; Sinha, S.K. Four area Load Frequency Control of interconnected hydro-thermal power system by Intelligent PID control technique. In Proceedings of the 2012 Students Conference on Engineering and Systems, Allahabad, India, 16–18 March 2012; pp. 1–6. [Google Scholar]
- Huang, T.; Satchidanandan, B.; Kumar, P.R.; Xie, L. An Online Detection Framework for Cyber Attacks on Automatic Generation Control. IEEE Trans. Power Syst. 2018, 33, 6816–6827. [Google Scholar] [CrossRef] [Green Version]
- Yammani, C.; Maheswarapu, S. Load Frequency Control of Multi-microgrid System considering Renewable Energy Sources Using Grey Wolf Optimization. Smart Sci. 2019, 7, 198–217. [Google Scholar]
- Doolla, S.; Bhatti, T.S. Load frequency control of an isolated small-hydro power plant with reduced dump load. IEEE Trans. Power Syst. 2006, 21, 1912–1919. [Google Scholar] [CrossRef]
- Semshchikov, E.; Hamilton, J.; Wu, L.; Negnevitsky, M.; Wang, X.; Lyden, S. Frequency control within high renewable penetration hybrid systems adopting low load diesel methodologies. Energy Procedia 2019, 160, 483–490. [Google Scholar] [CrossRef]
- Kumar, G.V.; Sarojini, R.K.; Palanisamy, K.; Padmanaban, S.; Holm-Nielsen, J.B. Large Scale Renewable Energy Integration: Issues and Solutions. Energies 2019, 12, 1996. [Google Scholar] [CrossRef] [Green Version]
- Rezkalla, M.; Pertl, M.; Marinelli, M. Electric power system inertia: Requirements, challenges and solutions. Electr. Eng. 2018, 100, 2677–2693. [Google Scholar] [CrossRef] [Green Version]
- Magdy, G.; Mohamed, E.A.; Shabib, G.; Elbaset, A.A.; Mitani, Y. Microgrid dynamic security considering high penetration of renewable energy. Prot. Control Mod. Power Syst. 2018, 3, 23. [Google Scholar] [CrossRef]
- Sarangan, S.; Singh, V.K.; Govindarasu, M. Cyber attack-defense analysis for automatic generation control with renewable energy sources. In Proceedings of the 2018 North American Power Symposium (NAPS), Fargo, ND, USA, 9–11 September 2018; pp. 1–6. [Google Scholar]
- Datta, A.; Bhattacharjee, K.; Debbarma, S.; Kar, B. Load frequency control of a renewable energy sources based hybrid system. In Proceedings of the 2015 IEEE Conference on Systems, Process and Control (ICSPC), Bandar Sunway, Malaysia, 18–20 December 2015; pp. 34–38. [Google Scholar]
- Datta, A.; Konar, S.; Singha, L.J.; Singh, K.M.; Lalfakzuala, A. A study on load frequency control for a hybrid power plant. In Proceedings of the 2017 Second International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, 22–24 February 2017; pp. 1–5. [Google Scholar]
- Xu, Y.; Li, C.; Wang, Z.; Zhang, N.; Peng, B. Load frequency control of a novel renewable energy integrated micro-grid containing pumped hydropower energy storage. IEEE Access 2018, 6, 29067–29077. [Google Scholar] [CrossRef]
- Hakimuddin, N.; Khosla, A.; Garg, J.K. Centralized and decentralized AGC schemes in 2-area interconnected power system considering multi source power plants in each area. J. King Saud Univ. Eng. Sci. 2020, 32, 123–132. [Google Scholar] [CrossRef]
- Arya, Y. AGC of restructured multi-area multi-source hydrothermal power systems incorporating energy storage units via optimal fractional-order fuzzy PID controller. Neural. Comput. Appl. 2019, 31, 851–872. [Google Scholar] [CrossRef]
- Arya, Y.; Kumar, N. Design and analysis of BFOA-optimized fuzzy PI/PID controller for AGC of multi-area traditional/restructured electrical power systems. Soft Comput. 2017, 21, 6435–6452. [Google Scholar] [CrossRef]
- Yousef, H.A. Power System Load Frequency Control: Classical and Adaptive Fuzzy Approaches; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef] [Green Version]
- Teixeira, A.; Pérez, D.; Sandberg, H.; Johansson, K.H. Attack models and scenarios for networked control systems. In Proceedings of the 1st International Conference on High Confidence Networked Systems; ACM: New York, NY, USA, 2012; pp. 55–64. [Google Scholar]
- Ding, D.; Han, Q.L.; Xiang, Y.; Ge, X.; Zhang, X.M. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing 2018, 275, 1674–1683. [Google Scholar] [CrossRef]
- Amin, S.; Cárdenas, A.A.; Sastry, S.S. Safe and secure networked control systems under denial-of-service attacks. In Proceedings of the International Workshop on Hybrid Systems: Computation and Control; Springer: Berlin/Heidelberg, Germany, 2009; pp. 31–45. [Google Scholar]
- Cetinkaya, A.; Ishii, H.; Hayakawa, T. An overview on denial-of-service attacks in control systems: Attack models and security analyses. Entropy 2019, 21, 210. [Google Scholar] [CrossRef] [Green Version]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-service (DoS) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Liu, J.; Gu, Y.; Zha, L.; Liu, Y.; Cao, J. Event-Triggered H∞ Load Frequency Control for Multiarea Power Systems Under Hybrid Cyber Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1665–1678. [Google Scholar] [CrossRef]
- Wang, Q.; Tai, W.; Tang, Y.; Zhu, H.; Zhang, M.; Zhou, D. Coordinated Defense of Distributed Denial of Service Attacks against the Multi-Area Load Frequency Control Services. Energies 2019, 12, 2493. [Google Scholar] [CrossRef] [Green Version]
- Jaafar, G.A.; Abdullah, S.M.; Ismail, S. Review of recent detection methods for HTTP DDoS attack. J. Comput. Netw. Commun. 2019, 2019, 1283472. [Google Scholar] [CrossRef] [Green Version]
- Zhong, X.; Jayawardene, I.; Venayagamoorthy, G.K.; Brooks, R. Denial of service attack on tie-line bias control in a power system with pv plant. IEEE Trans. Emerg. Top. Comput. Intell. 2017, 1, 375–390. [Google Scholar] [CrossRef]
- Girma, A.; Garuba, M.; Li, J.; Liu, C. Analysis of DDoS attacks and an introduction of a hybrid statistical model to detect DDoS attacks on cloud computing environment. In Proceedings of the 2015 12th International Conference on Information Technology-New Generations, Las Vegas, NV, USA, 13–15 April 2015; pp. 212–217. [Google Scholar]
- Sridhar, S.; Govindarasu, M. Model-based attack detection and mitigation for automatic generation control. IEEE Trans. Smart Grid 2014, 5, 580–591. [Google Scholar] [CrossRef]
- Jevtic, A.; Zhang, F.; Li, Q.; Ilic, M. Physics-and Learning-based Detection and Localization of False Data Injections in Automatic Generation Control. IFAC-PapersOnLine 2018, 51, 702–707. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2016, 8, 1630–1638. [Google Scholar] [CrossRef]
- Kontouras, E.; Tzes, A.; Dritsas, L. Impact analysis of a bias injection cyber-attack on a power plant. IFAC-PapersOnLine 2017, 50, 11094–11099. [Google Scholar] [CrossRef]
- Kontouras, E.; Tzes, A.; Dritsas, L. Cyber-attack on a power plant using bias injected measurements. In Proceedings of the 2017 American Control Conference (ACC), Seattle, WA, USA, 24–26 May 2017; pp. 5507–5512. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the 2009 47th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 30 September–2 October 2009; pp. 911–918. [Google Scholar]
- Fritz, R.; Zhang, P. Modeling and detection of cyber attacks on discrete event systems. IFAC-PapersOnLine 2018, 51, 285–290. [Google Scholar] [CrossRef]
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems: Designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Syst. Mag. 2015, 35, 93–109. [Google Scholar]
- Hoehn, A.; Zhang, P. Detection of replay attacks in cyber-physical systems. In Proceedings of the 2016 American Control Conference (ACC), Boston, MA, USA, 6–8 July 2016; pp. 290–295. [Google Scholar]
- Zhao, J.; Wang, J.; Yin, L. Detection and control against replay attacks in smart grid. In Proceedings of the 2016 12th International Conference on Computational Intelligence and Security (CIS), Wuxi, China, 16–19 December 2016; pp. 624–627. [Google Scholar]
- Hoehn, A.; Zhang, P. Detection of covert attacks and zero dynamics attacks in cyber-physical systems. In Proceedings of the 2016 American Control Conference (ACC), Boston, MA, USA, 6–8 July 2016; pp. 302–307. [Google Scholar]
- Li, W.; Xie, L.; Wang, Z. A novel covert agent for stealthy attacks on industrial control systems using least squares support vector regression. J. Electr. Comput. Eng. 2018, 2018, 1–14. [Google Scholar] [CrossRef] [Green Version]
- Smith, R.S. Covert misappropriation of networked control systems: Presenting a feedback structure. IEEE Control Syst. Mag. 2015, 35, 82–92. [Google Scholar]
- De Sá, A.O.; da Costa Carmo, L.F.R.; Machado, R.C.S. Covert attacks in cyber-physical control systems. IEEE Trans. Ind. Informat. 2017, 13, 1641–1651. [Google Scholar] [CrossRef] [Green Version]
- De Sá, A.O.; da Costa Carmo, L.F.R.; Machado, R.C.S. A controller design for mitigation of passive system identification attacks in networked control systems. J. Internet Serv. Appl. 2018, 9, 1–19. [Google Scholar] [CrossRef] [Green Version]
- Mohsenian-Rad, A.H.; Leon-Garcia, A. Distributed internet-based load altering attacks against smart power grids. IEEE Trans. Smart Grid 2011, 2, 667–674. [Google Scholar] [CrossRef]
- Hammad, E.; Khalil, A.M.; Farraj, A.; Kundur, D.; Iravani, R. Tuning out of phase: Resonance attacks. In Proceedings of the 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), Miami, FL, USA, 2–5 November 2015; pp. 491–496. [Google Scholar]
- Sargolzaei, A.; Yen, K.K.; Abdelghani, M.N. Preventing time-delay switch attack on load frequency control in distributed power systems. IEEE Trans. Smart Grid 2015, 7, 1176–1185. [Google Scholar] [CrossRef]
- Zhang, H.; Qi, Y.; Zhou, H.; Zhang, J.; Sun, J. Testing and defending methods against DoS attack in state estimation. Asian J. Control 2017, 19, 1295–1305. [Google Scholar] [CrossRef]
- Sinopoli, B.; Schenato, L.; Franceschetti, M.; Poolla, K.; Jordan, M.I.; Sastry, S.S. Kalman filtering with intermittent observations. IEEE Trans. Automat. Contr. 2004, 49, 1453–1464. [Google Scholar] [CrossRef]
- Wu, Y.; Li, Y.; Shi, L. A game-theoretic approach to remote state estimation in presence of a dos attacker. IFAC-PapersOnLine 2017, 50, 2595–2600. [Google Scholar] [CrossRef]
- Shen, Y.; Fei, M.; Du, D.; Zhang, W.; Stanković, S.; Rakić, A. Cyber Security Against Denial of Service of Attacks on Load Frequency Control of Multi-area Power Systems. In Advanced Computational Methods in Energy, Power, Electric Vehicles, and Their Integration; Springer: Berlin/Heidelberg, Germany, 2017; pp. 439–449. [Google Scholar]
- Peng, C.; Li, J.; Fei, M. Resilient Event-Triggering H∞ Load Frequency Control for Multi-Area Power Systems With Energy-Limited DoS Attacks. IEEE Trans. Power Syst. 2016, 32, 4110–4118. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. (TISSEC) 2011, 14, 13. [Google Scholar] [CrossRef]
- Kwon, C.; Liu, W.; Hwang, I. Security analysis for cyber-physical systems against stealthy deception attacks. In Proceedings of the 2013 American Control Conference, Washington, DC, USA, 17–19 June 2013; pp. 3344–3349. [Google Scholar]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. Revealing stealthy attacks in control systems. In Proceedings of the 2012 50th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 1–5 October 2012; pp. 1806–1813. [Google Scholar]
- Yang, Q.; Yang, J.; Yu, W.; An, D.; Zhang, N.; Zhao, W. On false data-injection attacks against power system state estimation: Modeling and countermeasures. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 717–729. [Google Scholar] [CrossRef]
- Chaojun, G.; Jirutitijaroen, P.; Motani, M. Detecting false data injection attacks in ac state estimation. IEEE Trans. Smart Grid 2015, 6, 2476–2483. [Google Scholar] [CrossRef]
- Bobba, R.B.; Rogers, K.M.; Wang, Q.; Khurana, H.; Nahrstedt, K.; Overbye, T.J. Detecting false data injection attacks on dc state estimation. In Proceedings of the Preprints of the First Workshop on Secure Control Systems, CPSWEEK, Stockholm, Switzerland, 12 April 2010; pp. 1–9. [Google Scholar]
- Bi, S.; Zhang, Y.J. Graphical methods for defense against false-data injection attacks on power system state estimation. IEEE Trans. Smart Grid 2014, 5, 1216–1227. [Google Scholar] [CrossRef]
- Esfahani, P.M.; Vrakopoulou, M.; Margellos, K.; Lygeros, J.; Andersson, G. A robust policy for automatic generation control cyber attack in two area power network. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; pp. 5973–5978. [Google Scholar]
- Esfahani, P.M.; Vrakopoulou, M.; Margellos, K.; Lygeros, J.; Andersson, G. Cyber attack in a two-area power system: Impact identification using reachability. In Proceedings of the 2010 American Control Conference, Baltimore, MD, USA, 30 June–2 July 2010; pp. 962–967. [Google Scholar]
- Giannini, M. Improving Cyber-Security of Power System State Estimators. 2014. Available online: https://www.diva-portal.org/smash/get/diva2:704601/FULLTEXT01.pdf (accessed on 7 June 2020).
- Liu, L.; Esmalifalak, M.; Ding, Q.; Emesih, V.A.; Han, Z. Detecting false data injection attacks on power grid by sparse optimization. IEEE Trans. Smart Grid 2014, 5, 612–621. [Google Scholar] [CrossRef]
- Huang, Y.; Li, H.; Campbell, K.A.; Han, Z. Defending false data injection attack on smart grid network using adaptive CUSUM test. In Proceedings of the 2011 45th Annual Conference on Information Sciences and Systems, Baltimore, MD, USA, 23–25 March 2011; pp. 1–6. [Google Scholar]
- Talebi, M.; Li, C.; Qu, Z. Enhanced protection against false data injection by dynamically changing information structure of microgrids. In Proceedings of the 2012 IEEE 7th Sensor Array and Multichannel Signal Processing Workshop (SAM), Hoboken, NJ, USA, 17–20 June 2012; pp. 393–396. [Google Scholar]
- Li, X.; Hedman, K.W. Enhancing Power System Cyber-Security with Systematic Two-Stage Detection Strategy. IEEE Trans. Power Syst. 2019, 35, 1549–1561. [Google Scholar] [CrossRef] [Green Version]
- Yang, L.; Li, Y.; Li, Z. Improved-ELM method for detecting false data attack in smart grid. Int. J. Electr. Power Energy Syst. 2017, 91, 183–191. [Google Scholar] [CrossRef]
- Wang, X.; Luo, X.; Zhang, Y.; Guan, X. Detection and Isolation of False Data Injection Attacks in Smart Grids via Nonlinear Interval Observer. IEEE Internet Things J. 2019, 6, 6498–6512. [Google Scholar] [CrossRef]
- Wang, X.; Luo, X.; Zhang, M.; Guan, X. Distributed detection and isolation of false data injection attacks in smart grids via nonlinear unknown input observers. Int. J. Electr. Power Energy Syst. 2019, 110, 208–222. [Google Scholar] [CrossRef]
- Rahman, M.A.; Mohsenian-Rad, H. False data injection attacks against nonlinear state estimation in smart power grids. In Proceedings of the 2013 IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Rahman, M.A.; Mohsenian Rad, H. False data injection attacks with incomplete information against smart power grids. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 3153–3158. [Google Scholar]
- Li, S.; Yılmaz, Y.; Wang, X. Quickest detection of false data injection attack in wide-area smart grids. IEEE Trans. Smart Grid 2014, 6, 2725–2735. [Google Scholar] [CrossRef]
- Chen, C.; Zhang, K.; Yuan, K.; Zhu, L.; Qian, M. Novel detection scheme design considering cyber attacks on load frequency control. IEEE Trans. Ind. Informat. 2017, 14, 1932–1941. [Google Scholar] [CrossRef]
- Khalaf, M.; Youssef, A.; El-Saadany, E. A Particle Filter-Based Approach for the Detection of False Data Injection Attacks on Automatic Generation Control Systems. In Proceedings of the 2018 IEEE Electrical Power and Energy Conference (EPEC), Toronto, ON, Canada, 10–11 October 2018; pp. 1–6. [Google Scholar]
- Ayad, A.; Khalaf, M.; El-Saadany, E. Detection of false data injection attacks in automatic generation control systems considering system nonlinearities. In Proceedings of the 2018 IEEE Electrical Power and Energy Conference (EPEC), Toronto, ON, Canada, 10–11 October 2018; pp. 1–6. [Google Scholar]
- Miloševič, J.; Tanaka, T.; Sandberg, H.; Johansson, K.H. Analysis and mitigation of bias injection attacks against a Kalman filter. IFAC-PapersOnLine 2017, 50, 8393–8398. [Google Scholar] [CrossRef]
- Luo, X.; Wang, X.; Zhang, M.; Guan, X. Distributed detection and isolation of bias injection attack in smart energy grid via interval observer. Appl. Energy 2019, 256, 113703. [Google Scholar] [CrossRef]
- Zhu, M.; Martinez, S. On the performance analysis of resilient networked control systems under replay attacks. IEEE Trans. Autom. Control 2013, 59, 804–808. [Google Scholar] [CrossRef] [Green Version]
- Stouffer, K.; Falco, J.; Scarfone, K. Guide to industrial control systems (ICS) security. NIST Spec. Publ. 2011, 800, 16. [Google Scholar]
- Sargolzaei, A.; Yen, K.; Abdelghani, M.N. Delayed inputs attack on load frequency control in smart grid. In Proceedings of the ISGT 2014, Washington, DC, USA, 19–22 February 2014; pp. 1–5. [Google Scholar]
- Jiang, L.; Yao, W.; Wu, Q.H.; Wen, J.Y.; Cheng, S.J. Delay-dependent stability for load frequency control with constant and time-varying delays. IEEE Trans. Power Syst. 2011, 27, 932–941. [Google Scholar] [CrossRef]
- Jia, H.; Yu, X.; Yu, Y.; Wang, C. Power system small signal stability region with time delay. Int. J. Electr. Power Energy Syst. 2008, 30, 16–22. [Google Scholar] [CrossRef]
- Wu, H.; Tsakalis, K.S.; Heydt, G.T. Evaluation of time delay effects to wide-area power system stabilizer design. IEEE Trans. Power Syst. 2004, 19, 1935–1941. [Google Scholar] [CrossRef]
- Milano, F.; Anghel, M. Impact of time delays on power system stability. IEEE Trans. Circuits Syst. I 2011, 59, 889–900. [Google Scholar] [CrossRef]








| Parameter | Parameter Description | Unit |
|---|---|---|
| Mechanical power change | p.u. | |
| Governor output change | p.u. | |
| Load change | p.u. | |
| Control signal | p.u. | |
| Tie-line active power deviation | p.u. | |
| Wind turbine input power change | p.u. | |
| Solar input power change | p.u. | |
| Wind turbine output power change | p.u. | |
| Photovoltaic (PV) output power change | p.u. | |
| Hydro turbine output power change | p.u. | |
| Frequency deviation of the power system | Hz | |
| R | Speed droop characteristic | Hz/p.u. |
| D | Equivalent damping coefficient | p.u./Hz |
| M | Equivalent inertia constant | p.u.-s |
| Governor time constant | s | |
| Turbine time constant | s | |
| Wind turbine time constant | s | |
| PV time constant | s | |
| Water starting time constant | s | |
| Frequency bias factor | p.u./Hz | |
| N | Number of control areas | - |
| Attack | Disclosure Resources | Disruption Resources | Model Knowledge | Practical Implementation Strategies |
|---|---|---|---|---|
| DoS Attack | Not needed | Sensor channel Actuator channel | Not needed | PMU packet losses |
| DDoS Attack | Not needed | Application and DNS sever | Not needed | SYN flood attack method |
| Bias Injection Attack (FDI variant) | Not needed | Frequency channel | Knowledge of closed- loop system, anomaly detector gains | Sensor or GPS spoofing |
| Replay Attack | Frequency and tie-line power flow channels | Frequency and tie-line power flow channels | Not needed | Cracking cryptographic algorithms, transmission data manipulations |
| Resonance Attack | Not needed | DAS channel, tie-line power flows | Complete system knowledge | Load manipulation through ELC or manual switching |
| Covert Attack | Sensor and actuator channels | Sensor and actuator channels | Complete system knowledge | Sensor and actuator data modification |
| TDS Attack | Not needed | Sensor and actuator channels | Complete system knowledge | Delaying data packets |
| Zero-dynamics Attack | Not needed | Actuator communication channels | Perfect knowledge of the zero-dynamics of the system | - |
| Defense Mechanism | Advantages | Disadvantages | LFC System for Analysis | Attack Point |
|---|---|---|---|---|
| DAELM algorithm- based data prediction [24] | Fast and accurate prediction, less prediction time and computational complexity, enhance real-time performance, | No RES integration | Single-area, area, three-area | Sensor channels |
| CNN prediction with VSN [72] | PV integrated, real-time VSN countermeasures | Real-time PMU data delivery is expensive | Single-area, two-area | Sensor channels |
| Resilient control strategy [14,30,40] | Event-triggered strategy [14], guaranteed exponential stability [30] | No RES integration | Single-area [14], two-area, three-area [30] | Sensor channel [14], additional control loop [30], both actuator and sensor channels [40] |
| Coordinated defense of DDoS attack using ACL-based fireworks and compensator controllers [70] | Improves overall control effect, complete attack defense cycle | ACL detection is weak for real-time performance, compensated control can be negative during little delay situations | Single-area | Application and DNS servers |
| Detection Technique | Advantages | Disadvantages | LFC System | Attack Point |
|---|---|---|---|---|
| Particle filter-based detection approach using SIS algorithm [118] | Considers non-linearities like time-delay and governor deadband | Resampling technique is needed | Two-area | Frequency and tie-line measurements |
| Luenberger observer with artificial neural network [27] | Fast, accurate, resilient toabrupt FDI and GPS spoofing, considers non-linearities | Needs system mathematical model | Two-area | PMU measurements |
| Cyber-attack detection and mitigation platform [33] ACE data using forecasted data | Scans real-time | Needs frequency correction multiplier | Three-area | ACE channel |
| Deep learning-based approach using long short term memory [75] (LSTM) networks | Trained LSTM network detects abnormal ACE patterns, not model-based | Needs accurate training data | Two-area | ACE channel |
| Dynamic water marking technique using control signal [48] | Detects complex attackers having complete system knowledge, hardware update of generation units are not needed | Applied to small-scale power systems | Four-area | Sensor and actuator channels |
| Set-theoretic approach [36] | Reveals adversaries in the presence of external disturbances and during transient system response | Small persistent signals can pass undetected | Two-area | Frequency measurements |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mohan, A.M.; Meskin, N.; Mehrjerdi, H. A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems. Energies 2020, 13, 3860. https://0-doi-org.brum.beds.ac.uk/10.3390/en13153860
Mohan AM, Meskin N, Mehrjerdi H. A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems. Energies. 2020; 13(15):3860. https://0-doi-org.brum.beds.ac.uk/10.3390/en13153860
Chicago/Turabian StyleMohan, Athira M., Nader Meskin, and Hasan Mehrjerdi. 2020. "A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems" Energies 13, no. 15: 3860. https://0-doi-org.brum.beds.ac.uk/10.3390/en13153860